AI has become a double-edged sword in the thriving sector of cybersecurity, acting as a potent defensive tool but also appearing as a targeted means for increasingly sophisticated cyberattacks. With that rapid rise of AI-driven threats, the urgent need for more effective counter-measurements has been of paramount necessity.
According to Avast statistics, 90% of first-quarter threats in 2024 have been in close connection with social engineering, with a noticeable increase in deep fake audio and AI-generated videos. The disruptive technology giant – OpenAI also admitted that their system was under the malicious influence of China, North Korea, Russia, and Iran while these subjects were trying to create content inciting phishing campaigns and generating malware.
So, to cope with these growing threats of AI-based cyberattacks, what measures should businesses adopt? Let’s find out 6 key Actions that could help compete with AI-driven cyberattacks to shield your system more effectively.
Utilizing AI itself to identify potential threats
Cutting-edge threat detection systems developed by AI have been revolutionizing the cybersecurity sector considerably. These systems are designed to detect unusual behaviors and hazardous activities that traditional tools might possibly overlook.
- – Detecting unusual behaviors: AI systems provide the fastest alerts about potential threats by identifying abnormal activities, such as irregular network access or suspicious logins, by analyzing an enormous amount of data.
- – Identifying Malicious Activities: AI can spot malicious activities such as malware, phishing, and suspicious contacts by making analyses and connecting data from distinct sources.
- – Examples of AI-Powered Security Systems: Numerous cybersecurity enterprises make use of AI-driven solutions, such as Darktrave, Cylance, or Endpoint Protection from Symantec, to recognize threats better.

To impede AI-driven cyberattacks, it is essential for organizations to prioritize updating and monitoring their security systems on a regular basis:
- – Regular Security Audits: Conduct regular security audits and vulnerability assessments to recognize and minimize the risks related to weaknesses in the system.
- – Continuous Learning and Adaptation: To deal with newly existing threats, AI systems need to be updated regularly. With the view to improving its accuracy, machine learning models should also be retrained with new data.
- – Proactive Monitoring: Companies should carry out regular monitoring activities to detect threats in no time. This includes establishing alert modes and automated response mechanisms.
- – Integrating Threatening Information: To identify and respond to acknowledged threats, AI systems should integrate threatening information into their own systems.
Multi-factor Authentication (MFA)
Multi-factor Authentication (MFA) is the security method that provides a second additional layer of authentication beyond a standard password. It requires users to give one or more additional authentication factors, such as One-time password (OTP), fingerprint, or facial recognition.
The benefits of Multi-factor Authentication (MFA) are rather transparent: it increases security barriers by mitigating risks of stolen passwords. MFA also protects accounts from unauthorized access even when the password is invaded, ensuring that confidential information remains secure.
With its role in averting AI-driven cyberattacks, especially those targeted in passwords, Multi-Factor Authentication (MFA) is considered an integral method. In that case, although AI can guess or steal passwords, attackers will still need a second authentication factor, making it an uphill task to breach accounts. For instance, in case passwords are leaked through AI-powered phishing attacks, OPT or biometric authentication will still be able to protect targeted accounts.

To effectively implement MFA within an organization, you have to follow these best practices:
- – Comprehensive Deployment: Apply the MFA function for not only bank accounts or emails but for all critical systems and apps.
- – Personnel Training: Make sure that all employees grasp and follow the MFA procedure, including its guide and benefits.
- – Diverse Authentication Factors Usage: To strengthen the security system, collaborate several different authentication factors, such as OPT and biometric authentication.
- – Regular Updates: Ensure that the MFA system is checked and updated on a regular basis to address all new threats.
By means of implementing MFA, organizations could enhance security, mitigate risks from AI-driven cyberattacks, and protect personal information and priceless assets.
Zero-Knowledge Credentials
Zero-knowledge cryptography is a technique that allows one party to demonstrate that they know a certain value without disclosing, ensuring sensitive data never be leaked.
Zero-knowledge cryptography protects information by verifying only necessary parts, not requiring users’ to share all personal data. This is conducive to guaranteeing users’ privacy.
Zero-knowledge cryptography can be applied in a variety of different fields, such as identity verification and data protection. For example, users can prove that they are over 18 years old during the identity verification without revealing their exact birthday. Not only does this process protect the personal information of users but it also puts a restraint on the risks of exposing significant data.
Advanced-Data Encryption
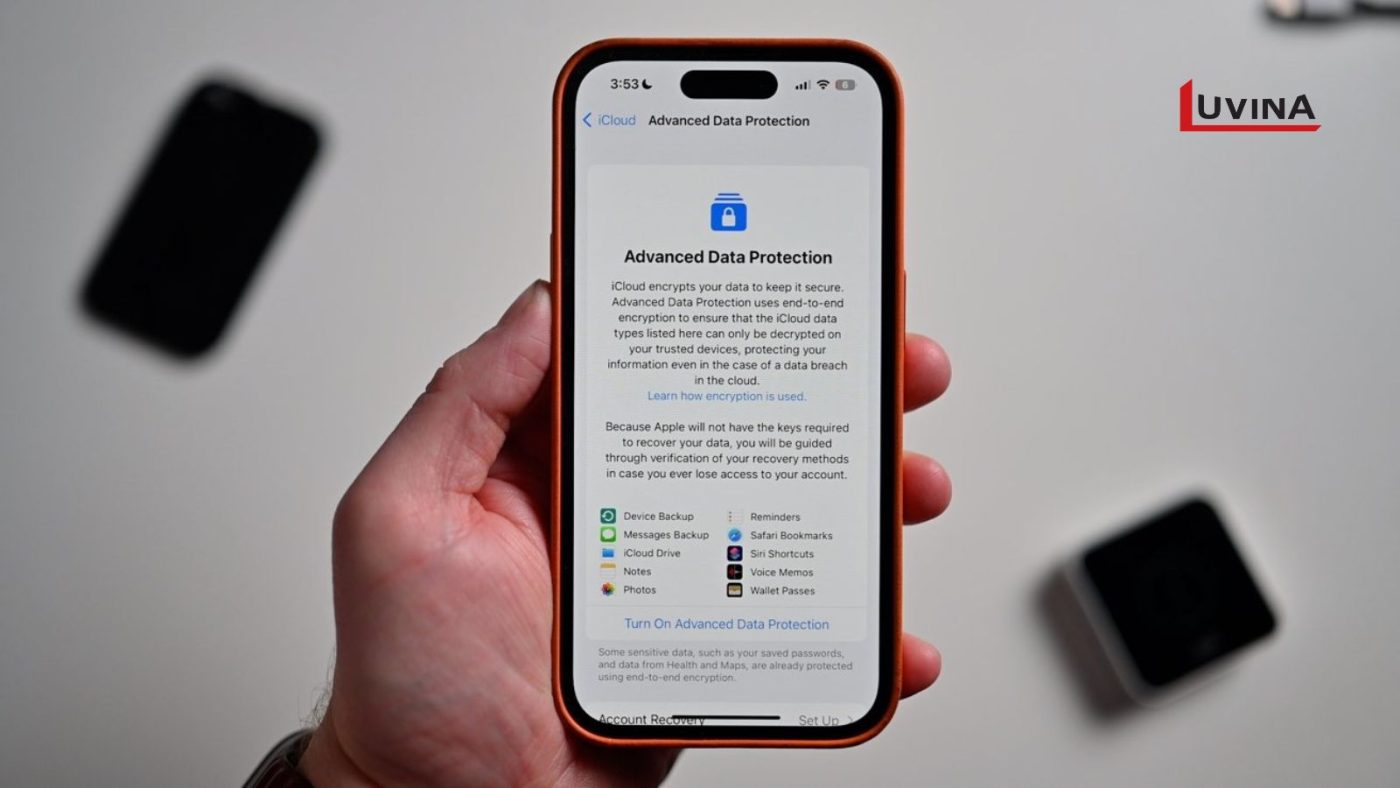
Encryption is an indispensable tool in protecting data from unauthorized access, especially in the age of rising sophisticated AI-driven cyberattacks. The utilization of state-of-the-art encryption algorithms such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) will pave the way for the utmost assurance of data privacy. Advanced encryption protocols like TLS (Transport Layer Security) also play an integral part in protecting data during transmission.
To make sure that data is always in a safe position, it is necessary to implement end-to-end encryption in all systems including communication channels and data storage systems. This ensures data can only be decrypted by the intended recipient, deterring theft and interference from outsiders.
The Human Factor in Security
Humans have always been the most vulnerable and weakest element in the security chain. Therefore, raising users’ awareness and knowledge of the cybersecurity threats is of greatest emergency to mitigate possible risks. Users need to be equipped with essential skills to identify signs of phishing, deep fakes, and other AI-generated scams. This helps them respond promptly and eliminates the possibility of becoming a victim.
Organizing training lessons regularly and providing up-to-the-minute materials on the latest cyberattack risks is incredibly crucial. In addition, users should also be encouraged to get involved in online courses, and seminars and receive notifications about the most up-to-date threats so that they can reinforce their security know-how and skills.
The importance of Collaboration among Organizations, Governments, and Security Experts.
The collaborating relationships among organizations, governments, and security experts are the contributing factors to combating AI-based cyberattacks for the reason that the defense capacities, source sharing, and security strategies will be enhanced through working together. Organizations can swiftly detect and respond to attacks by sharing information about possible threats, attacks, and new defense strategies. This creates a more powerful and robust network, boosting defense abilities and minimizing attack likelihoods.

To ensure that security experts and organizations can exchange information with each other effectively, specialized networks and forums are of necessity. These communities will not only update newly existing threatening potentials but also help participants share their security skills.
Conclusion
In the realm of cybersecurity, AI has demonstrated its superior dual role as both a striking defensive tool and a fundamental element for sophisticated cyberattacks but also a contributor to formidable threats. To shield the systems and data from these escalating threats, we must adopt a comprehensive strategy comprising both technological measurements and enhancing public awareness tools.
With that in mind, Luvina Software promises to provide robust security solutions and in-depth consultancy on this matter to help your company compete against detrimental AI-driven cyberattacks. Our strengths lie in services correlated with advanced threat detection, implementation of MFA, and advanced data encryption.

Don’t let the emerging technological threats put your companies in jeopardy. Contact Luvina Software to receive bespoke consultation and customized security solutions’ implementation right now.









Read More From Us?
Sign up for our newsletter
Read More From Us?
Sign up for our newsletter