Every business, regardless of size, must increase its digital defenses against cyber threats. Small businesses, in particular, face unique challenges in ensuring robust IT security solutions. Addressing these concerns involves a strategic approach that combines appropriate measures and effective practices. From understanding specific risks to implementing reliable security software and training employees, there are countless steps small businesses can take to strengthen their cybersecurity. Adopting these strategies not only fortifies their digital resilience but also ensures the protection of critical data and operations, aligning with the best practices in IT security solutions for small businesses.
Understanding Your Risks in IT Security Solutions for Small Businesses
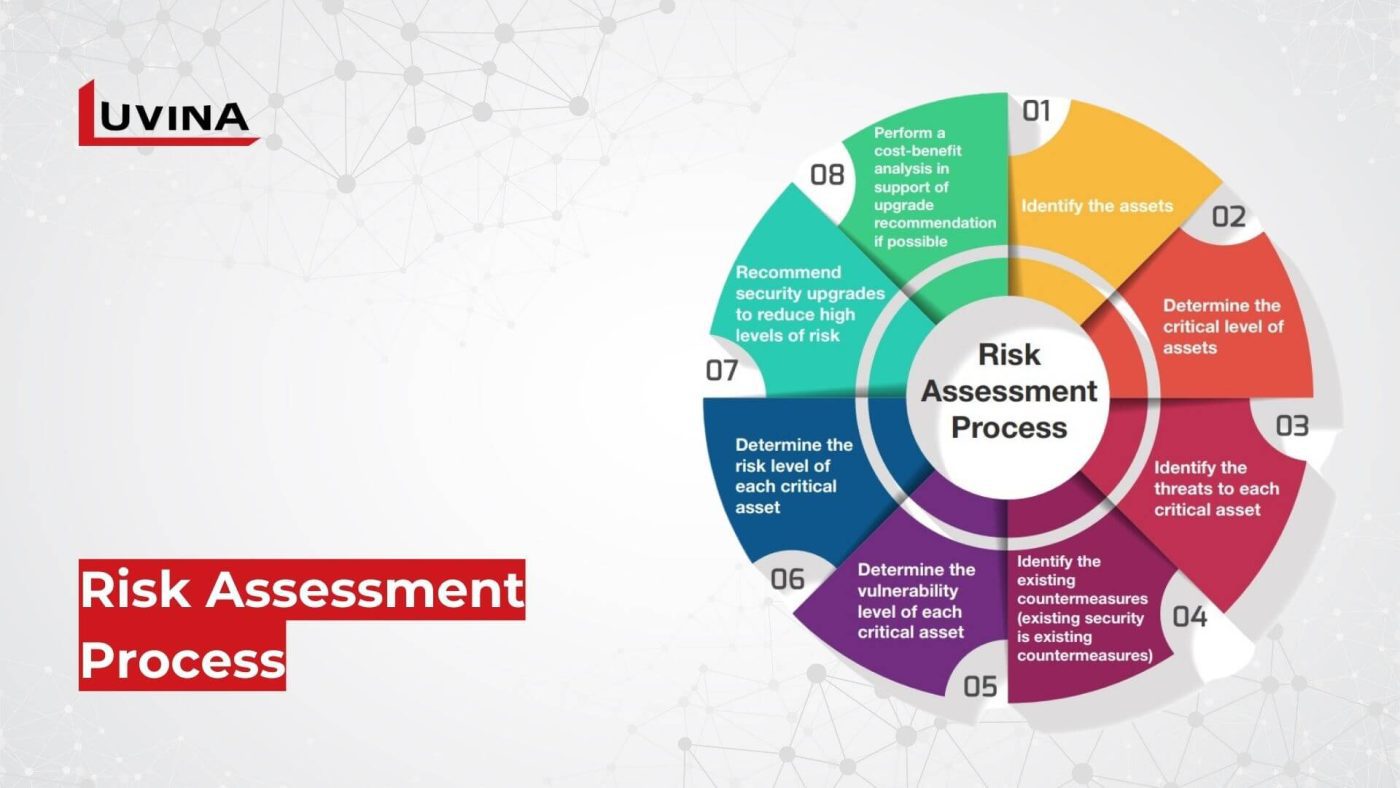
Initiate your security journey with a comprehensive risk assessment. This pivotal step involves identifying critical data assets, and potential vulnerabilities within your system, and foreseeing potential threats looming over your business. This meticulous examination lays the groundwork for prioritizing and implementing targeted security measures to safeguard your valuable assets effectively.
>> Also Read: A Comprehensive Guide to IT Security Risk Management
Implement Basic Security Measures
Commence by integrating core security practices into your operations. This includes fortifying your defenses with robust, regularly updated passwords and embracing the additional layer of protection offered by two-factor authentication. Ensure your systems and software are consistently updated, fortifying resilience against emerging threats and vulnerabilities.
Invest in Reliable Security Software
Select reliable antivirus, anti-malware, and firewall solutions to safeguard your systems against potential threats. Regularly update these security tools to maintain their effectiveness and conduct periodic scans to detect and eliminate any lurking vulnerabilities or malware. Consistent vigilance is crucial in maintaining a secure IT environment.
Backup Your Data Regularly
Creating a robust backup strategy is essential to protect vital data. Regularly back up your critical information to secure off-site or cloud-based locations. This approach helps prevent data loss in the event of system failures, cyber-attacks, or breaches, ensuring that your business can quickly recover and resume operations.

Educating and Training Employees in IT Security Solutions for Small Businesses
Regular security awareness training is pivotal in mitigating risks associated with human error in security breaches. Educating employees about cybersecurity best practices enhances their understanding of potential threats and the importance of safeguarding sensitive data. Through comprehensive training programs, staff members gain insights into identifying suspicious activities, recognizing phishing attempts, and adhering to robust security protocols. This knowledge equips them to act as an additional line of defense, fortifying the overall security posture of the organization.
Secure Your Network
Creating secure Wi-Fi networks is crucial to protect against unauthorized access. Encryption adds an extra layer of security, making data unreadable if intercepted. Segmenting networks helps contain breaches, limiting access to sensitive areas. Implementing a Virtual Private Network (VPN) ensures secure remote access, encrypting data transmitted between the device and the network, even on public connections. This setup shields sensitive information and communications, maintaining confidentiality and integrity across remote connections.
Adopt Cloud Security Measures
Selecting reputable cloud service providers ensures robust security measures. Encrypting data before storing it in the cloud adds a layer of protection, rendering the information unreadable if intercepted. Implementing stringent access controls limits data access to authorized personnel only. Regularly reviewing and managing user access helps prevent unauthorized entry or misuse of sensitive information stored in the cloud.

Create and Enforce Security Policies
Creating clear and concise security policies is vital to establishing guidelines for acceptable use, data handling, and incident response. These policies should outline the dos and don’ts, specify how sensitive information is handled, and detail the steps to take in case of a security incident. Consistently enforcing these policies across the organization ensures a unified approach to security measures and adherence to established protocols.
Consider Managed Security Services
Outsourcing security to managed service providers offers small businesses cost-effective access to expert security services, including continuous monitoring and support. These managed IT security services provide specialized expertise and ongoing surveillance, alleviating the burden on internal resources and ensuring round-the-clock protection against potential threats.
Regularly Review and Update Security Measures
Cyber threats constantly evolve, underscoring the need for regular security posture evaluations and updates. Ensure continual reassessment of security measures, staying abreast of emerging threats and solutions to maintain a proactive approach in safeguarding your systems against evolving risks.
Seek Expert Guidance When Needed
Feel free to seek advice from IT security consulting companies or experts when evaluating your security requirements or executing new security measures. Their expertise can provide valuable insights and guidance tailored to your specific business needs, ensuring a more effective and robust security framework.

Safeguarding Your Small Business with IT Security Solutions
By diligently implementing these actionable strategies and recommendations, small businesses can bolster their overall IT security infrastructure. These measures serve as robust shields against potential risks and threats, fortifying the organization’s defense mechanisms. Moreover, these proactive steps ensure that the security posture is fortified without imposing undue strain on the company’s resources, thereby fostering a resilient and protected digital environment.









Read More From Us?
Sign up for our newsletter
Read More From Us?
Sign up for our newsletter