In today’s digital landscape, safeguarding sensitive data and networks is paramount for businesses. IT Security Monitoring Services play a pivotal role in identifying, analyzing, and responding to cyber threats. These services encompass a range of activities including continuous monitoring, threat detection, incident response, and vulnerability management. Understanding these services is crucial for any organization aiming to enhance its cybersecurity posture.
What is IT security monitoring services?
IT security monitoring services are a crucial component of any organization’s cybersecurity strategy. They help organizations identify, analyze, and respond to cyber threats before they can cause significant damage.

IT security monitoring services involved in these key activities:
1. Continuous Monitoring
Utilizes tools and systems to constantly observe networks, systems, applications, and endpoints for any signs of suspicious activities, vulnerabilities, or breaches.
2. Threat Detection
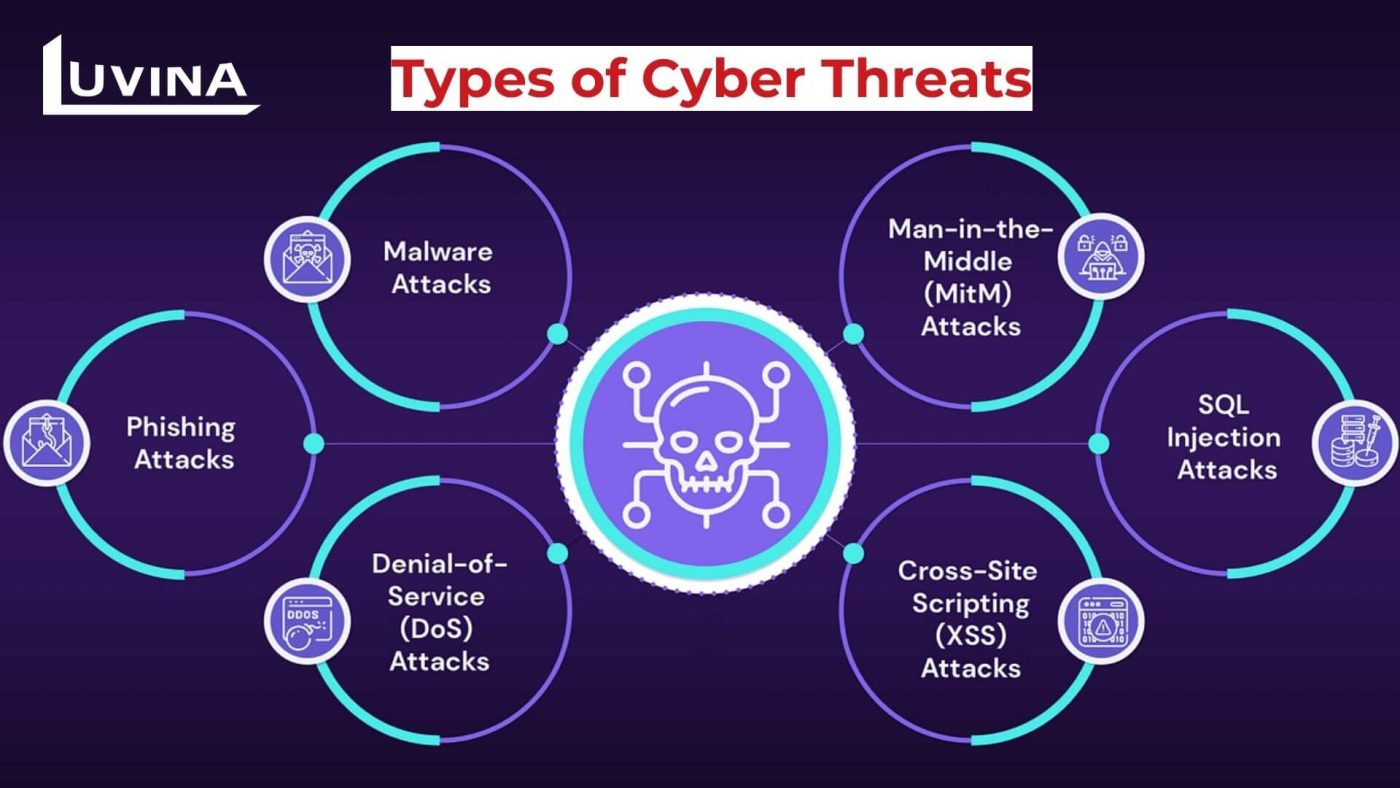
Identifies and analyzes potential security threats, including malware, phishing attempts, unusual network traffic, unauthorized access attempts, etc.
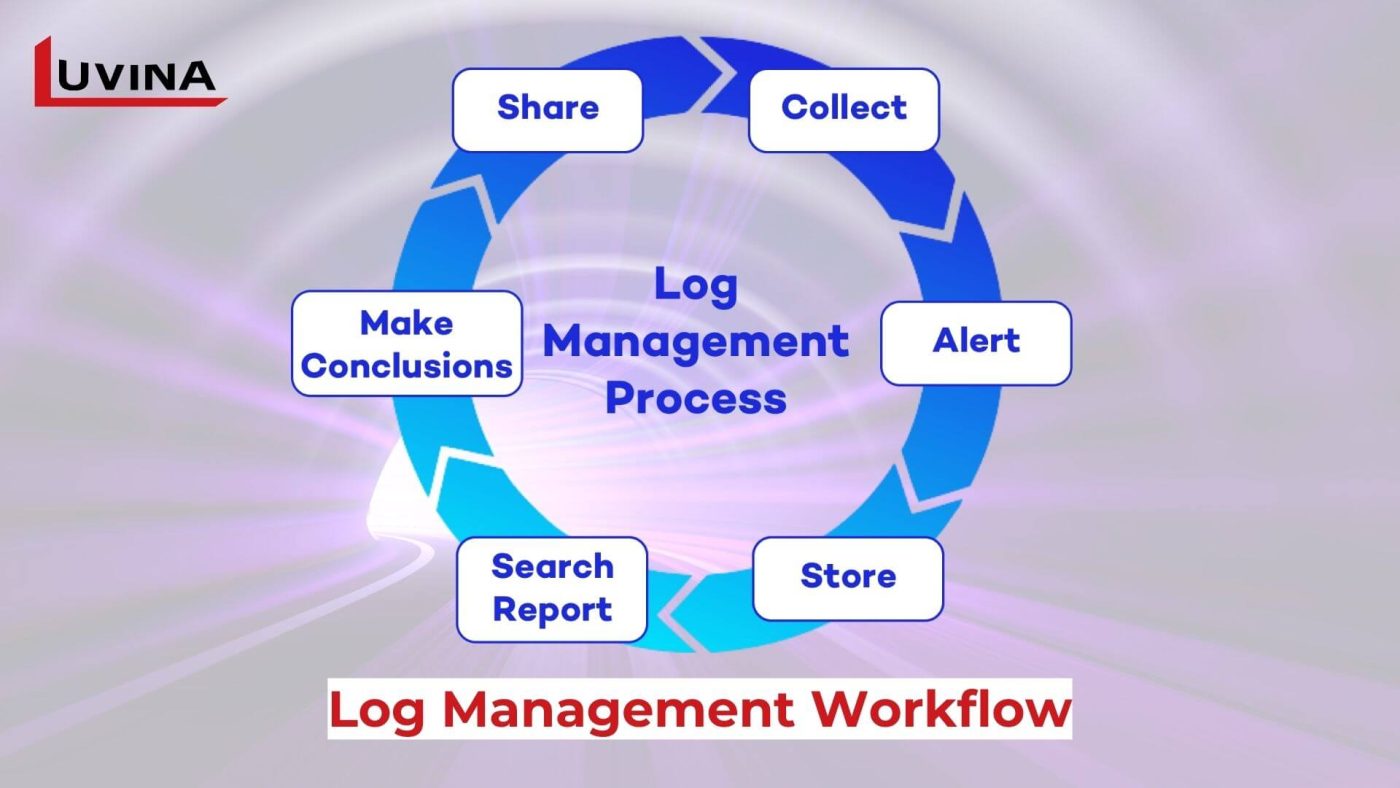
3. Log Management
Collects and analyzes logs generated by various systems and applications to detect patterns or anomalies that could indicate security issues.
4. Incident Response
Provides a structured approach to handling security incidents. Once a threat is detected, this service initiates response protocols to mitigate the impact and prevent further damage.
5. Vulnerability Management
Scans and assesses systems and applications for vulnerabilities. This includes regular updates, patch management, and addressing known security weaknesses.
6. SIEM (Security Information and Event Management)
Integrates security information management and security event management. SIEM tools collect and analyze security data from multiple sources to provide a holistic view of an organization’s security posture.
7. Threat Intelligence
Incorporates external threat intelligence sources to enhance the monitoring process, helping to identify emerging threats and trends.
8. Compliance Monitoring
Ensures that the organization adheres to relevant regulatory standards and internal security policies.
9. Managed Detection and Response (MDR)
Offers a more comprehensive and proactive approach by combining monitoring with rapid incident response and threat hunting.
10. Real-time Alerts and Reporting
Provides real-time alerts to security teams and stakeholders when potential threats or unusual activities are detected. Regular reports may also be generated to provide insights and trends.
Benefits of IT security monitoring services
IT security monitoring services offer a multifaceted shield against cyber threats by actively overseeing an organization’s digital infrastructure. These services play a pivotal role in safeguarding sensitive data, promptly detecting suspicious activities, and mitigating potential breaches before they escalate. Continuously monitoring networks, systems, and applications provides real-time insights into security incidents, ensuring quick responses to potential threats. Moreover, these services not only enhance the overall security posture but also enable businesses to comply with industry regulations and maintain customer trust by swiftly addressing security issues.
Improved threat detection: Security monitoring services can help organizations to detect cyber threats more quickly and effectively.
Reduced response time: By identifying threats early, organizations can take action to mitigate the damage and prevent further attacks.
Improved compliance: Security monitoring services can help organizations to comply with industry regulations and standards.
Reduced costs: By preventing cyberattacks, organizations can save money on data recovery, legal fees, and other costs associated with a breach.
Increased peace of mind: Security monitoring services can provide organizations with peace of mind knowing that their systems are monitored 24/7.
Types of IT security monitoring services
IT security monitoring services encompass a diverse array of strategies and tools designed to protect digital assets from potential threats. These services commonly involve various monitoring methods such as network monitoring, which oversees data traffic for anomalies and unauthorized access; endpoint monitoring, focused on individual devices to identify suspicious behavior; log management, aggregating and analyzing system logs for security insights; and cloud security monitoring, safeguarding cloud-based resources and data.
Additionally, threat intelligence services track emerging risks and vulnerabilities, while security information and event management (SIEM) systems collect and analyze security-related data from multiple sources. These monitoring services work collectively to ensure a comprehensive defense against cyber threats across various digital fronts.
Managed Security Service Providers (MSSPs): MSSPs offer a comprehensive suite of security monitoring services, including threat detection, incident response, and vulnerability management.
Security Information and Event Management (SIEM): SIEM solutions collect and analyze security data from multiple sources to provide a unified view of the organization’s security posture.
Security Orchestration, Automation, and Response (SOAR): SOAR solutions automate the response to security incidents, which can help organizations respond more quickly and effectively.
Who needs IT security monitoring services?
IT security monitoring services are crucial for virtually every entity operating in the digital realm. This includes businesses of all sizes, government agencies, educational institutions, healthcare providers, financial institutions, and even individual users. Any entity that uses digital systems, and networks, or stores sensitive information is susceptible to cyber threats. Hence, implementing IT security monitoring services is essential to safeguard data, prevent unauthorized access, detect potential breaches, and ensure compliance with industry regulations. From multinational corporations handling extensive data to individuals managing personal information online, everyone benefits from robust IT security monitoring to shield against evolving cyber risks.
>> See more: Navigating IT Security Consulting: A Comprehensive Guide
Conclusion
In summary, the adoption of IT security monitoring services stands as a fundamental shield against the constantly evolving landscape of cyber threats. Organizations, regardless of their scale or industry, benefit immensely from the deployment of these services. Through such investments, businesses fortify their security infrastructure, minimizing vulnerabilities, and mitigating potential cyberattacks. Not only does this fortification enhance their security posture, but it also bolsters their resilience against threats, safeguarding their critical data and preserving the integrity of their operations.









Read More From Us?
Sign up for our newsletter
Read More From Us?
Sign up for our newsletter